Encrypted messaging developer finds arbitrary code execution hole that could be used to cast doubt on reports from Cellebrite tools.
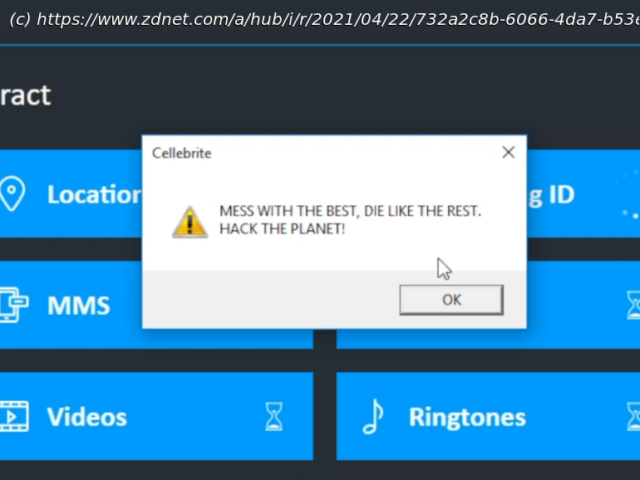
Phone scanning and data extraction company Cellebrite is facing the prospect of app makers being able to hack back at the tool, after Signal revealed it was possible to gain arbitrary code execution through its tools. Cellebrite tools are used to pull data out of phones the user has in their possession. “By including a specially formatted but otherwise innocuous file in an app on a device that is then scanned by Cellebrite, it’s possible to execute code that modifies not just the Cellebrite report being created in that scan, but also all previous and future generated Cellebrite reports from all previously scanned devices and all future scanned devices in any arbitrary way (inserting or removing text, email, photos, contacts, files, or any other data), with no detectable timestamp changes or checksum failures,” Signal CEO Moxie Marlinspike wrote. “This could even be done at random, and would seriously call the data integrity of Cellebrite’s reports into question.” Usually, when vulnerabilities of this type are found, the issue is disclosed to the maker of the software to fix, but since Cellebrite makes a living from undisclosed vulnerabilities, Marlinspike raised the stakes.