PowerShell script tells you if you’re Windows OS is safe from MDS attacks.
Today, a group of academics and security researchers disclosed a new type of vulnerability class impacting Intel CPUs — named Microarchitectural Data Sampling (MDS) attacks.
Similar to the now infamous Meltdown and Spectre flaws from last year, MDS attacks allow threat actors to retrieve data that is being processed inside Intel CPUs, even from applications an attacker’s code wouldn’t normally interact.
Four MDS attacks have been revealed today, with Zombieload considered the most dangerous of them all:
To safeguard systems, users must install Intel CPU microcode updates, but also OS-level updates. Microsoft, along with other OS makers, have already released OS patches today.
Intel has released microcode updates to motherboard and OEM firmware vendors already, and they should be made available to users as part of OEM firmware updates in the future.
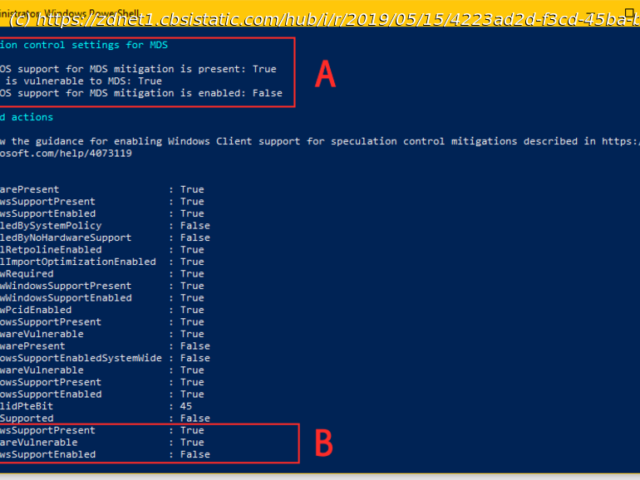
Last year, Microsoft released a PowerShell script to help system administrators detect if Meltdown and Spectre patches have installed and are working correctly.
Today, Microsoft updated that same script to support the new MDS attacks, which just like the Meltdown and Spectre vulnerabilities, are also flaws in the speculative execution process, and can be detected the same way.
Below are the steps to download and use the PowerShell script, as well as information to the way results should be interpreted.
1) Open a PowerShell terminal with admin rights.