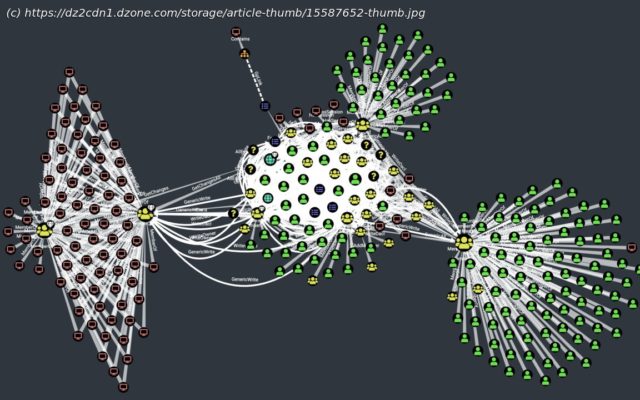
Learn how to identify AD problems with high-privilege Kerberos users, domain control object ownership, and domain users using BloodHound FOSS.
Join the DZone community and get the full member experience. Active Directory (AD) is Microsoft’s identity and access management software that controls which users have access to the systems and resources on a network. It’s a popular target for attackers because getting control of AD allows them to deploy malware, steal sensitive information or do other nasty things in a way that’s very difficult for defenders to detect or block. Making AD more secure involves fixing security flaws within the environment that allow attackers to get in – but first defenders need to identify what those flaws are. AD’s built-in tooling makes it very difficult to see which users have privileges to which systems and objects. So many security issues, even very dangerous ones, simply go unnoticed. Luckily for defenders, several common AD security issues are quite easy to fix once they’ve been identified. These “low-hanging fruit” issues allow defenders to reduce the risk exposure of their AD environment relatively easily. Here are three of the most common security issues across AD environments, their impacts, and how defenders can find and fix them. I’ll be explaining how to do this using BloodHound, a free and open-source tool (of which I am a co-creator) for mapping Microsoft Active Directory and Azure Active Directory, but you can follow the same steps using a different tool. The Kerberoast attack was first identified by security researcher Tim Medin in 2014. It extracts service account credential hashes from Active Directory for offline cracking and can be carried out by any user without sending packets to the target. When highly-privileged users in a target environment are vulnerable to this attack, they give threat actors a short route to seizing control of Active Directory. My colleagues and I see this issue in virtually all of the real-world AD environments we examine. Having high-privileged users vulnerable to Kerberoasting creates a great deal of security risk, but identifying those vulnerable privileged users is extremely difficult using only AD’s built-in tools.