«Legal» Spyware: How Pegasus Uses iPhones to Repeatedly Target Victims Through Zero-Click iOS Exploits That Require No Interaction
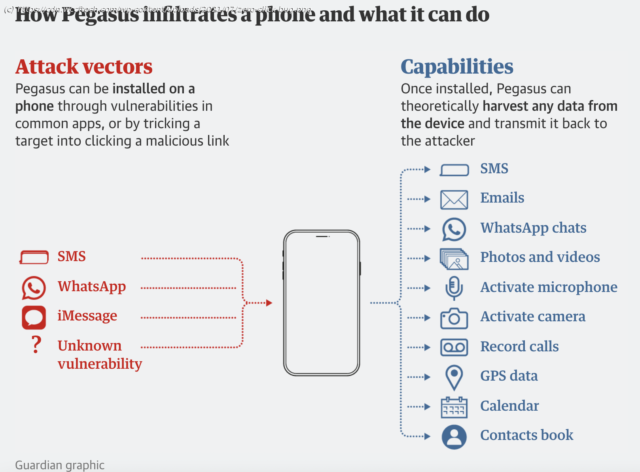
A new report released yesterday gave us an alarming look into how the spyware sold by the Israeli surveillance company NSO Group was involved in targeted attacks against lawyers, journalists, opposition politicians, and activists across the world by different authoritarian governments. While NSO Group has been at the center of many similar reports in the past, the extent to which its Pegasus spyware enables unlawful surveillance and human rights abuses wasn’t fully known. The firm continues to claim Pegasus is only used to «investigate terrorism and crime» without leaving a trace behind. However, the Forensic Methodology Report released over the weekend by over 17 media organizations in 10 countries with the technical support of Amnesty International’s Security Lab that carried out an in-depth forensic analysis of several devices from human rights defenders and journalists around the world, proves that is not true. Facebook Tried to Buy Surveillance Technology Used to Spy on Apple Users The list includes «hundreds of business executives, religious figures, academics, NGO employees, union officials and government officials, including cabinet ministers, presidents and prime ministers,» the Guardian’s report added. The list also includes numbers of over 180 journalists, including that of a freelance Mexican reporter, Cecilio Pineda Birto, who was murdered after his killers were able to locate him at a carwash. His phone was never recovered so forensic analysis isn’t possible to fully confirm if his phone was infected with Pegasus. Forensics analysis of a small number of phones whose numbers appeared on the leaked list showed more than half had traces of Pegasus. Focusing on Android and iOS smartphones, the forensic records revealed zero-click attacks that require zero interaction from the target. One of the most alarming findings of this report is that even the most latest iPhones running the most latest iOS versions were successfully exploited. «Most recently, a successful ‘zero-click’ attack has been observed exploiting multiple zero-days to attack a fully patched iPhone 12 running iOS 14.