Microsoft has created confusion about minimum hardware requirements for Windows 11, but there’s more to firmware security than TPMs.
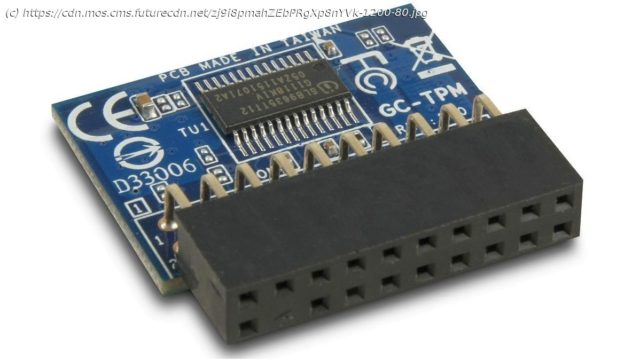
Microsoft has confused just about everyone with its minimum hardware requirements for Windows 11. At the heart of the confusion is a piece of technology known as a Trusted Platform Module, or TPM. The job of TPM chips is to perform cryptographic operations that provide security at a hardware level and verify the authenticity of a system at launch. They also feature various mechanisms to make them resistant to tampering. Among other specifications relating to the CPU, RAM and storage, Windows 11 will require all machines to feature TPM 2.0 support, either built into the CPU or in the form of an additional chip connected to the motherboard. The announcement sent PC owners scrambling to find out whether their device supports TPM and, in some cases, how to switch it on in the BIOS. And the subsequent revelation that Windows 11 can technically be installed on incompatible machines only added to the confusion. However, one company is scratching its head over the TPM decision for a different reason. According to Jorge Myszne, founder and CEO of semiconductor startup Kameleon, TPM is already an anachronistic technology. “TPM is from 2003; it was good enough 20 years ago, but think about everything that has changed in terms of infrastructure over the last two decades,” he told TechRadar Pro. “The main challenge is that the TPM is a passive device; while you can store data there and nobody can see it, in order to do something with that data the software needs access. And if the software has access, an attacker can gain access too.” Founded in 2019 and backed by Xilinx, a pioneer in the field of programmable SoCs, Kameleon’s objective is to reverse the dynamics of cybercrime, by handing the advantage to the defender. Although the company is yet to bring a product to market, it is working on a piece of hardware called a Proactive Security Processing Unit (ProSPU) that it hopes can combat the threat of firmware attacks, which are increasing in volume and sophistication.